
Facial Recognition vs. Other Authentication Methods
In a world where nearly everything is connected — from banking and healthcare to entertainment and communication — protecting our digital identities has become more important than ever. Whether you're logging into your email, accessing sensitive business data, or unlocking your smartphone, authentication is the invisible gatekeeper standing between your information and potential threats.
As cyberattacks become more sophisticated, the old methods of simply entering a username and password are no longer enough. Data breaches, identity theft, and unauthorized access are constant risks in today’s online landscape. In fact, weak or stolen credentials remain one of the leading causes of security incidents across the globe.
That’s why the way we verify our identities—known as authentication—has evolved. From passwords and PINs to biometrics and multi-factor authentication, organizations and individuals alike are rethinking how they balance security, convenience, and privacy.
One of the most prominent developments in recent years is facial recognition—a technology that uses a person’s unique facial features as a digital key. It’s fast, user-friendly, and already embedded in millions of devices worldwide. But is it really the best option? And how does it compare to other authentication methods?
In this post, we’ll explore the key differences between facial recognition and traditional authentication techniques, looking at how each performs in terms of security, user experience, cost, and more. Whether you're a developer, business owner, or curious user, understanding the strengths and limitations of these methods can help you make smarter, more secure choices.
What Is Facial Recognition?
Facial recognition is a biometric technology that identifies or verifies a person’s identity using their face. It analyzes facial features—such as the distance between the eyes, the shape of the jawline, or the contour of the cheekbones—to create a unique digital signature of an individual’s appearance.
Unlike traditional security methods like passwords or PIN codes, facial recognition doesn’t require physical input from the user. A simple glance at a camera can authenticate a person in a matter of seconds. This hands-free, contactless nature makes it increasingly attractive in our fast-paced, convenience-driven world.
How Facial Recognition Works
Facial recognition typically involves a multi-step process:
Detection. The system locates a face in a photo or video feed. This step ensures that the subject is a face and not another object.
Analysis. Once a face is detected, the system maps key facial landmarks. These might include the position of the eyes, nose, and mouth, along with unique measurements such as the width of the forehead or the depth of eye sockets.
Conversion to Data. The analyzed features are translated into a mathematical model, often called a faceprint—similar to how fingerprints are digitized.
Matching. This faceprint is then compared to a database of known faces to verify or identify the person. Advanced systems can perform this comparison in real-time, even from a crowd.
Modern facial recognition systems often rely on AI and machine learning to improve accuracy over time. They can adapt to changes in lighting, angles, and even subtle variations in facial expressions or aging.
Use Cases and Popularity of Facial Recognition
Facial recognition has moved far beyond the realm of sci-fi and become a part of everyday life. It’s widely used in:
Smartphones and Devices. Unlocking phones, authorizing app purchases, and logging into secure platforms.
Airports and Border Control. Speeding up identity verification and enhancing passenger security.
Law Enforcement. Assisting in criminal investigations by identifying suspects in video footage or crowds.
Retail and Marketing. Personalizing customer experiences or analyzing foot traffic through in-store analytics.
Banking and Fintech. Enabling secure, password-free transactions and identity verification for accounts.
Its popularity stems from the seamless balance between convenience and security. As facial recognition systems become more accurate and accessible, their adoption continues to grow across industries—from healthcare and education to entertainment and finance.
Overview of Other Authentication Methods
While facial recognition has made a splash in the world of digital security, it's far from the only player in the game. A variety of authentication methods are in use today, each with its own advantages, limitations, and ideal use cases. From simple passwords to physical tokens, these technologies have been shaping how we protect data and digital identities for decades.
Let’s explore the most common authentication methods used alongside—or instead of—facial recognition.
Password-Based Authentication
Passwords are the oldest and most familiar form of digital authentication. A password is a secret combination of characters, created by the user, that grants access to a system when correctly entered.
While easy to implement and widely adopted, password-based systems come with major downsides. Weak or reused passwords are a leading cause of security breaches. Even strong passwords can be compromised through phishing, brute-force attacks, or data leaks. Despite these flaws, passwords remain a go-to method for many systems due to their simplicity and low cost.
PIN Codes
Personal Identification Numbers (PINs) are typically shorter than passwords and consist only of numbers, making them quicker to enter, especially on devices like ATMs or smartphones.
PINs offer a layer of security similar to passwords but are often limited in length, which makes them more susceptible to guessing or brute-force attacks. However, when combined with device-level encryption or biometric checks, PINs can be an effective secondary security measure.
Fingerprint Scanning
Fingerprint authentication uses the unique patterns of ridges and valleys on a person’s fingertips to verify identity. This method is popular in smartphones, laptops, and secure access systems.
Fingerprint scanning offers a good balance between convenience and security. It’s fast, easy to use, and harder to forge than passwords. However, it’s not infallible—high-resolution images or silicone molds can potentially spoof some scanners, and physical injury or wear can sometimes reduce scanner accuracy.
Two-Factor Authentication (2FA)
Two-Factor Authentication enhances security by requiring users to provide two types of verification: something they know (like a password) and something they have (like a phone or token), or something they are (like a fingerprint or face).
Common implementations include entering a code sent via SMS, using an authentication app, or plugging in a hardware key. 2FA significantly increases protection against unauthorized access, even if a password is compromised.
Its only drawback is the potential inconvenience for users—especially if they lose access to their second factor. However, the security benefits typically outweigh this minor friction.
Smart Cards and Tokens
Smart cards and hardware tokens are physical devices that store encrypted credentials. They’re commonly used in corporate environments, government agencies, and highly regulated industries where strong authentication is critical.
These methods offer robust security by storing credentials offline, making them difficult to hack remotely. Smart cards can also be used in conjunction with PINs or biometrics for multi-factor authentication. On the downside, physical tokens can be lost or stolen, and managing them at scale can be costly and complex.
Use Case Scenarios
No single authentication method fits every situation perfectly. The ideal solution often depends on the specific context—whether you're securing a mobile app, a government facility, or a customer login portal. Let’s look at where facial recognition shines and where other methods might offer better performance or practicality.
When Facial Recognition Makes Sense
Facial recognition is best suited for scenarios where speed, convenience, and minimal physical contact are priorities. Its ability to verify identity passively and quickly makes it an attractive option in many modern settings:
Smartphones and consumer devices. Unlocking phones, authorizing app purchases, and logging into secure platforms becomes effortless with a glance. This method balances convenience and security, especially when enhanced with liveness detection.
Airport security and border control. Facial recognition is increasingly used in e-passport gates and customs checks to streamline passenger flow and reduce wait times. It offers quick identity verification without the need for physical documents.
Workplace access control. In corporate or high-security environments, facial recognition can replace key cards or badges, reducing the risk of lost or stolen credentials.
Healthcare and patient management. In hospitals or clinics, facial recognition can be used to securely match patients to records without requiring ID cards or forms—saving time and reducing errors.
Public safety and surveillance. Law enforcement agencies use facial recognition to identify persons of interest in public spaces. While controversial, it’s often applied to enhance security in large gatherings or transportation hubs.
Where Other Methods Might Be Better
Despite its advantages, facial recognition is not always the best choice. There are some situations where traditional or alternative methods may be more suitable—whether due to technical limitations, regulatory restrictions, or user demographics.
Privacy-sensitive environments. In regions with strict privacy laws or sectors where data protection is critical, such as mental health services or legal firms, storing facial data can raise ethical and legal concerns. Passwords, PINs, or smart cards may be preferred in these cases.
Low-cost or resource-limited settings. For small businesses or startups, implementing facial recognition might be too costly. Simpler methods like passwords, 2FA apps, or fingerprint scanners provide effective security with lower overhead.
Users with accessibility challenges. Not all users may be able or willing to use facial recognition—due to disabilities, religious practices, or privacy concerns. In such cases, offering alternative methods ensures inclusivity and user trust.
Choosing the Right Tool for the Job
Ultimately, the best authentication method is the one that fits your use case, user base, and risk profile. Facial recognition is powerful, but it’s not a silver bullet. In many cases, the most secure and user-friendly approach is a combination of technologies—like facial recognition with fallback to PIN or 2FA when needed.
Conclusion
As digital threats evolve and user expectations continue to rise, the importance of secure, efficient, and user-friendly authentication has never been greater. From traditional passwords to cutting-edge facial recognition, the tools we use to protect our digital identities each come with unique strengths—and trade-offs.
Summary of Key Insights
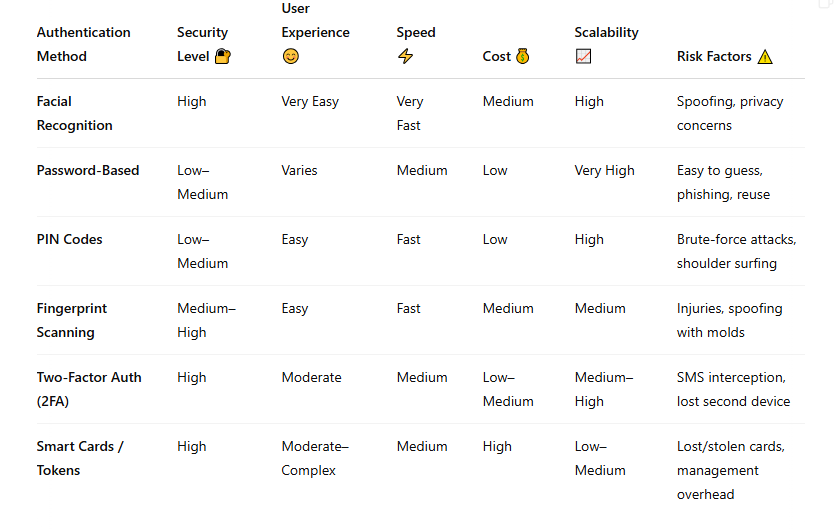
Facial recognition offers unmatched speed, convenience, and a seamless user experience. It’s ideal for scenarios that demand quick, contactless authentication—such as unlocking smartphones, securing workplaces, or streamlining airport processes.
Passwords and PIN codes, while still widely used, face significant security challenges and are often the weakest link in modern authentication systems.
Fingerprint scanning strikes a good balance between usability and security but can be limited by environmental factors or hardware availability.
Two-Factor Authentication (2FA) dramatically increases security by requiring a second verification step, though it may introduce some friction for users.
Smart cards and hardware tokens are highly secure and effective for enterprise-level applications but can be costly and harder to manage at scale.
Each method shines in specific contexts—what works for a government agency might not suit an e-commerce app or a health startup.
Choosing the Right Method for Your Needs
There’s no one-size-fits-all solution when it comes to authentication. The “best” method depends on a range of factors:
Security requirements. Is your application high-risk or handling sensitive data?
User environment. Will users be authenticating remotely, on shared devices, or in low-tech regions?
User experience. Do you need something frictionless, or are your users comfortable with extra steps?
Budget and infrastructure. What resources do you have for implementation and ongoing maintenance?
Regulatory environment. Are there legal restrictions around biometrics or data storage in your region?
For most businesses and applications, a layered approach—combining facial recognition with backup methods like PINs or 2FA—offers both resilience and flexibility. This ensures that security isn’t compromised when a single method fails or becomes unavailable.
