
How to Fool and Avoid Facial Recognition in Public Places
There is a growing trend of using facial recognition technology in public spaces such as retail malls, stadiums, and airports. While this technology can be used for security and convenience, it also raises concerns about privacy and surveillance.
Consider a bustling city department store during the holiday season, teeming with shoppers. Amidst the crowd, there is a regular customer – let’s call him John – browsing through the electronics section. As he examines a pair of headphones, the store’s facial recognition system, designed to detect and prevent theft, suddenly triggers an alert. The system, having erroneously matched John’s features with those of a known shoplifter from its database, flags him as a suspect.
Store security, relying on the system’s accuracy, escorts John to a private room for questioning. Confused and embarrassed, John insists on his innocence. Meanwhile, the actual shoplifter could be taking advantage of the situation, continuing their malicious activities unnoticed.
John is detained for an hour, missing important meetings and enduring the stress of false accusation. After reviewing the surveillance footage, it becomes clear that the system made an error, and John is released with an apology. However, the damage is done.
This scenario underscores the potential consequences of relying too heavily on automated systems without adequate human oversight. In this blog, we will provide tips on how to protect your privacy in the age of facial recognition. We will explore how facial recognition works and how to avoid it.
Real Cases of using Facial Recognition in Public Places

Science fiction has given way to reality as facial recognition technology is already a commonplace feature of daily life, particularly in public areas. It is fundamentally changing how we interact with our surroundings. The following is a list of its most notable applications.
Enhanced Security and Surveillance
Airports and border checkpoints are using facial recognition to make passenger screening more efficient and secure. For instance, at John F. Kennedy International Airport in New York, facial recognition technology is being used to streamline the boarding process. Passengers can simply scan their faces at self-service kiosks to verify their identities and print their boarding passes. This has significantly reduced wait times and made the boarding process more efficient.
Law enforcement agencies are also taking advantage of this technology to identify and capture suspects swiftly, thereby improving public safety. For example, in London, the Metropolitan Police Service is using facial recognition technology to help identify and apprehend suspects. The technology has been used to solve a number of high-profile crimes.
Even casinos are on board, using it to detect banned patrons and keep an eye out for any dubious behavior: the Venetian Macao casino in Macau uses facial recognition technology to detect banned patrons and identify suspicious behavior. The technology has helped the casino to prevent banned gamblers from entering the premises and to deter potential cheats.
Convenient and Personalized Experiences
Smart cities are integrating facial recognition to provide frictionless access to public amenities, like bike-sharing programs and government buildings. Imagine being able to unlock your bike from a bike-sharing program or enter a government building simply by looking at a camera. No more fumbling for keys or cards!
Retailers are not far behind, as they experiment with the technology to offer customers a more personalized shopping experience with custom deals and suggestions. Some stores are using facial recognition to identify customers and automatically charge their accounts. You could also receive personalized discounts and recommendations based on your past purchases.
The healthcare sector is also exploring its use for accurate patient identification, which could lead to fewer mistakes and more streamlined operations.
Public Safety and Crowd Management

When it comes to managing large crowds at events like concerts or sports games, facial recognition systems are invaluable for monitoring attendees, spotting potential disruptors, and maintaining overall safety. This technology also aids in locating lost children amidst the crowds or swiftly identifying individuals in the unfortunate event of an accident, facilitating prompt medical attention.
It is also proving useful in urban settings to help find missing individuals, identify accident victims, and prevent criminal activities.
Access Control and Identity Verification
In the hustle of daily life, the convenience and security of facial recognition are increasingly evident. Residential complexes now offer a seamless entry experience, where residents simply walk up to the gate and are recognized instantly, eliminating the need for keys or access cards. Office buildings have embraced this technology to streamline entry processes, making the morning rush smoother for employees.
For banks and financial institutions, facial recognition has become a cornerstone of customer security. It is not uncommon to walk into a bank and have your identity verified through a quick scan, ensuring that only you can access your accounts and authorize transactions.
Meanwhile, educational institutions are leveraging this technology to modernize attendance tracking. Instead of the traditional roll call, students can be automatically checked in as they enter the classroom. This system also bolsters campus security, as it can quickly identify individuals and prevent unauthorized access, creating a safer environment for students and staff alike.
Why do People Want to Avoid Facial Recognition in Public Places?
People may have various reasons for wanting to avoid facial recognition in public places, and here are a few:
Privacy concerns. People could find it unsettling to think that they are being watched over all the time and that their every action is being tracked. For instance, a person strolling through a mall might not want their whereabouts and purchasing behaviors to be observed without permission.
Data security. Facial recognition systems may capture data that is vulnerable to hacking or misuse. The possibility of identity theft in the event that a financial institution’s database is breached and unauthorized access is gained to personal accounts is a real-life concern.
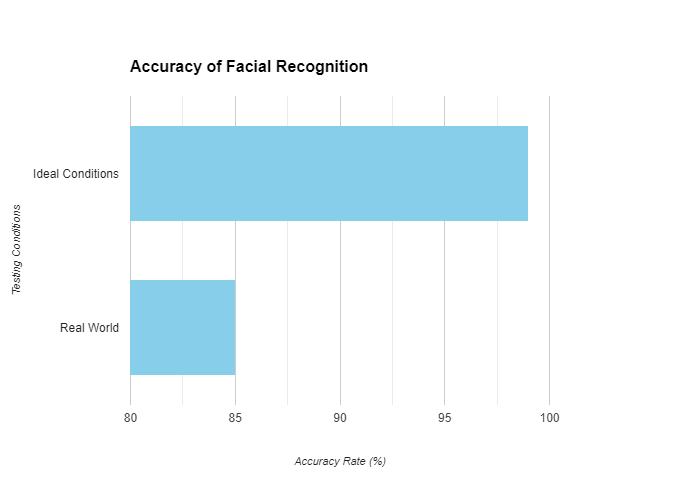
Misidentification. Facial recognition technology is not perfect and occasionally misidentifies people, which can cause confusion or discomfort. Consider a situation when a system error causes someone to be falsely detected as a shoplifter in a store, leading to their detention.
Loss of anonymity. In a society that values individual freedom, the ability to remain anonymous in public spaces is important to many. People participating in a peaceful protest might want to keep their involvement private, but facial recognition could expose their identities.
Techniques to Avoid Facial Recognition
To avoid facial recognition, individuals can employ various techniques that alter their appearance or disrupt the technology. Here an outline of such methods.
Physical Alterations

The "Incognito" mask by Ewa Nowak
Makeup techniques. Applying cosmetics strategically can drastically change a person’s face features, making facial recognition software difficult to use. For example, applying contrasting patterns on the face might disrupt the facial contours’ continuity, making it more difficult for computers to match the face to the available data.
Hairstyle changes. Hairstyle changes can also have an impact on facial recognition. A new hairstyle or haircut that covers up facial features, such as forehead-covering bangs, can make it more difficult for the system to recognize the important facial landmarks.
Accessories (hats, glasses, masks). Wearing a wide-brimmed hat or large sunglasses can shield crucial facial features from detection. Masks, especially those designed to thwart facial recognition, can be very effective, as they cover significant portions of the face.
Clothing Choices

Patterned clothing. Certain patterns, especially complex or irregular ones, can create visual noise that confuses facial recognition systems when worn near the face, like on a high-collared jacket or a scarf. For example, you can wear a scarf with a special design based on an algorithmic pattern known as a CV Dazzle camouflage, which is specifically designed to break up the expected facial symmetry and features that facial recognition systems look for. The complex patterns on the scarf interfere with the camera’s algorithms. The system is looking for the usual arrangement of eyes, nose, and mouth, but the scarf’s pattern disrupts the facial contours, making it difficult for the system to lock onto the facial landmarks.
Hoodies and scarves. Pulling a hoodie tight around the face or wrapping a scarf can obscure the shape of the head and neck, making it difficult for systems to identify a person based on their silhouette.
Technology-Based Solutions
Infrared LED glasses. Glasses equipped with infrared LEDs can emit light that is invisible to the human eye but can blind facial recognition cameras. These glasses are equipped with small infrared LEDs positioned around the frame, near the eyes, and on the bridge of the nose. When activated, these LEDs emit infrared light, which is invisible to the human eye but highly detectable by digital cameras. The infrared light creates bright spots on the footage captured by surveillance cameras, effectively obscuring facial features.
Reflective materials. Clothing or accessories made with reflective materials can bounce back the light from cameras, causing glare that can obscure the face in digital images. The special reflective fabric is embedded with thousands of tiny glass beads that act like mirrors, reflecting light directly back towards its source. When you walk through a city monitored by surveillance cameras, the reflective clothing works as a shield against facial recognition. The cameras, which often use infrared light to capture clear images even in low-light conditions, are met with a glare from your cap or jacket. The reflected light creates bright spots and flares in the digital image.
Anti-surveillance devices. There are gadgets designed specifically to emit signals or patterns that interfere with the cameras’ ability to capture a clear image of the face, rendering the wearer unidentifiable. For example, you can carry a small, discreet device that can be clipped onto clothing or worn as a pendant. This device is equipped with a series of LED lights that emit complex patterns and signals across the visible and infrared spectrums. When you walk through a public space monitored by surveillance cameras, the device activates and begins to emit its pattern. The lights flash in a rapid sequence that is specifically designed to disrupt digital camera sensors. The emitted signals create a dynamic, unpredictable pattern that confuses the camera’s exposure settings and autofocus, resulting in blurred or distorted images.
These techniques represent a range of options that people might consider if they wish to maintain their privacy and avoid being identified by facial recognition technology in public spaces.
Conclusion
In conclusion, the rapid advancement of facial recognition technology presents a double-edged sword, offering benefits for security and convenience while posing significant risks to privacy and civil liberties. As we have explored in this article, there are a variety of methods available for individuals to safeguard their anonymity and personal freedom. From clothing and accessories designed with reflective materials to disrupt camera imaging, to specialized gadgets emitting signals that confound facial recognition algorithms, the tools to maintain privacy are as innovative as the technology they aim to outsmart.
However, it is crucial to remember that the goal is not to demonize technology but to promote a dialogue about its ethical use and the importance of protecting individual rights in a digital age. As we navigate this complex landscape, it's imperative for citizens, technologists, and policymakers to work together to establish guidelines that balance security needs with the fundamental right to privacy. By staying informed and proactive, we can enjoy the benefits of technology without sacrificing our personal freedoms.
